Sunday 17 July 2022
Last month, a massive botnet-induced distributed denial of service (DDoS) attack has hit the Internet, two years after the record-breaking 23 million requests per second (RPS) attack on AWS. This latest attack against Clouflare peaked at an astounding 26 million RPS.
Botnets such as Mirai, Hajime and Reaper have long been used in DDoS attacks, but the Internet is increasingly threatened by a new breed of DDoS attacks — ones that don’t rely on massive remote control networks. This attack, like the Amazon attack and Github attack (1.35tb per second in 2018) was notable not just because it was so large, but also because it was delivered without the help of a botnet.
The attack targeted a customer website using Cloudflare’s Free plan. Similar to the previous 15M rps attack, this attack also originated mostly from Cloud Service Providers as opposed to Residential Internet Service Providers, indicating the use of hijacked virtual machines and powerful servers to generate the attack — as opposed to much weaker Internet of Things (IoT) devices. Cloudflare stated:
The 26M rps DDoS attack originated from a small but powerful botnet of 5,067 devices. On average, each node generated approximately 5,200 rps at peak. To contrast the size of this botnet, we’ve been tracking another much larger but less powerful botnet of over 730,000 devices. The latter, larger botnet wasn’t able to generate more than one million requests per second, i.e. roughly 1.3 requests per second on average per device. Putting it plainly, this botnet was, on average, 4,000 times stronger due to its use of virtual machines and servers.
The DDoS Attack was Fast and Furious
As you can see from the image of the attack below, it was fast, sharp but was quickly mitigated or not able to sustain the resources needed to maintain a prolonged DDoS attack above 20M rps:
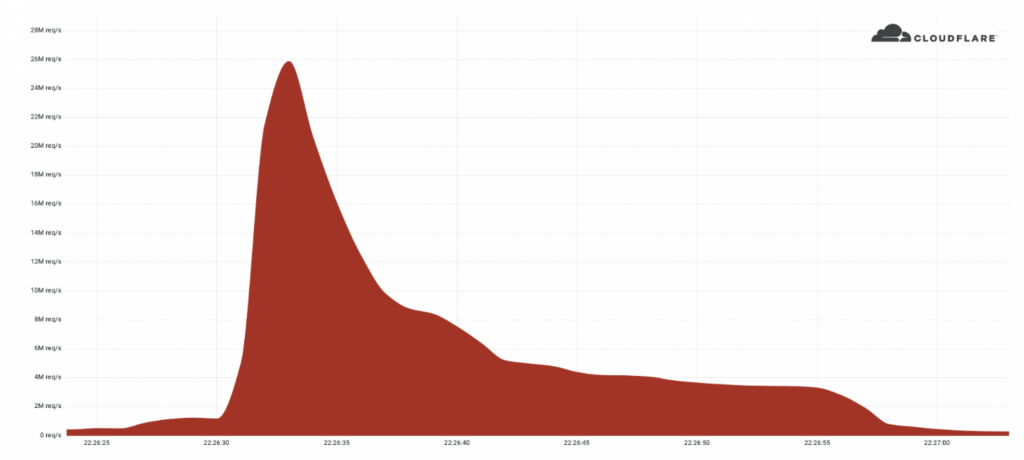
credit: Cloudflare
How do DDoS Attacks Occur
DDoS attacks are delivered via either direct or reflected attacks. Direct attacks use botnets comprised of hijacked IoT devices, computers and/or servers. These botnets then target the DNS infrastructure with a massive amount of queries or packets. This can be done using either real or spoofed IP addresses. The most common use of botnets is to clog up networks by sending a deluge of useless requests in an attempt to crash or hijack any machine on the network.
A reflection attack involves an attacker spoofing a target’s IP address and sending a request for information, primarily using the User Datagram Protocol (UDP) or in some caes, the Transmission Control Protocol (TCP). The server then responds to the request, sending an answer to the target’s IP address. This “reflection”—using the same protocol in both directions—is why this is called a reflection attack.
DNS: How can brands defend against such large attacks?
Most volumetric attacks rely on some kind of amplification such as DNS reflection or Network Time Protocol amplification attacks where the requesting IP address is spoofed as the target’s and massive amounts of traffic is returned at relatively little cost to the attacker. The scale of attack means that organisations need to consider:
- Capacity, Choose Wisely: The capacity of their DNS network to deal with such large-scale attacks. Most enterprise DNS networks would simply not cope with a 2 TB per second attack, so understanding your network’s capacity is important. A domain name Registrar’s DNS will not survive such an attack. Most would not. Only a few dedicated DNS networks in the world can manage an attack of such scale.
- Shaping and Filtering: A strong DDoS defense system implements traffic shaping, which involves clamping traffic loads with multi-modal detection and mitigation strategies in order to protect the service from falling over, but separates the bad queries from the legitimate ones.
UltraDNS defense
UltraDNS has certainly been tested by attacks and has created one of the world’s largest and strongest DNS networks that can withstand multiple times the largest DNS DDoS attack recorded to date. They are constantly increasing their infrastructure bandwidth, security, filtering tools and capacity to stay ahead of new DNS DDos attacks. They stand by their 100% uptime guarantee and offer features such as:
- UltraDNS Firewall
A recursive DNS service that is designed to block threats at point of contact, before they hit your network. - SiteBacker (Failover/monitoring)
This feature is UltraDNS’s failover and monitoring service that requires no dedicated hardware to implement. SiteBacker runs health checks on resources and automatically directs traffic to an alternate resource in the event the primary IP/host fails. This solution can also be paired with other UltraDNS services. - Traffic Controller (Weighted Round Robin)
Traffic Controller is a weighted load balancing feature that supports Weighted and traditional Round Robin based on percentages. Any host that hits critical status receives a 50% reduction in traffic. If a resource fails, the record won’t be returned. - Directional DNS (GeoDNS)
This option is UltraDNS’s Geolocation service which routes traffic according to end-user location. They offer 3,500 locations around the world to choose from and allow you to combine locations. This feature also lets you restrict access based on region. - Apex Alias
Apex Alias is a technique that allows users to provide CNAME functionality at the root of their domain. - Secondary DNS
Neustar UltraDNS supports traditional Secondary DNS - Recursive DNS
Neustar Ultra DNS offers a free recursive public DNS.
About brandsec
Brandsec is a corporate domain name management and brand protection company that looks after many of Australia, New Zealand and Asia’s top publicly listed brands. We provide monitoring and enforcement services, DNS, SSL Management, domain name brokerage and dispute management and brand security consultation services.

