Introduction to Unphish
Phishing has evolved into an omni-channel issue. With hundreds of thousands of registrars, ISPs, content hosts, and social media platforms operating under diverse policies, laws, and languages, the removal of phishing content is often a slow, cumbersome process for brands and their targeted customers.
Discovering a phishing website, malicious domain name, or fake social media property is just the first step; the subsequent process to remove the infringing content is typically slow and fraught with challenges. We have decided to tackle this decentralized and frustrating reporting of phishing properties and online abuse. Our goal is to simplify the process and provide our customers with a unified enforcement interface, regardless of the registrar, host, or social media platform involved.


First look
Unveiling Unphish
Interested in joining Unphish Beta?
Register your interest and experience the power of Unphish
Remove Phishing Content Quickly and Effortlessly with Unphish
Sign up for early access to Unphish Beta and experience best in class takedown service
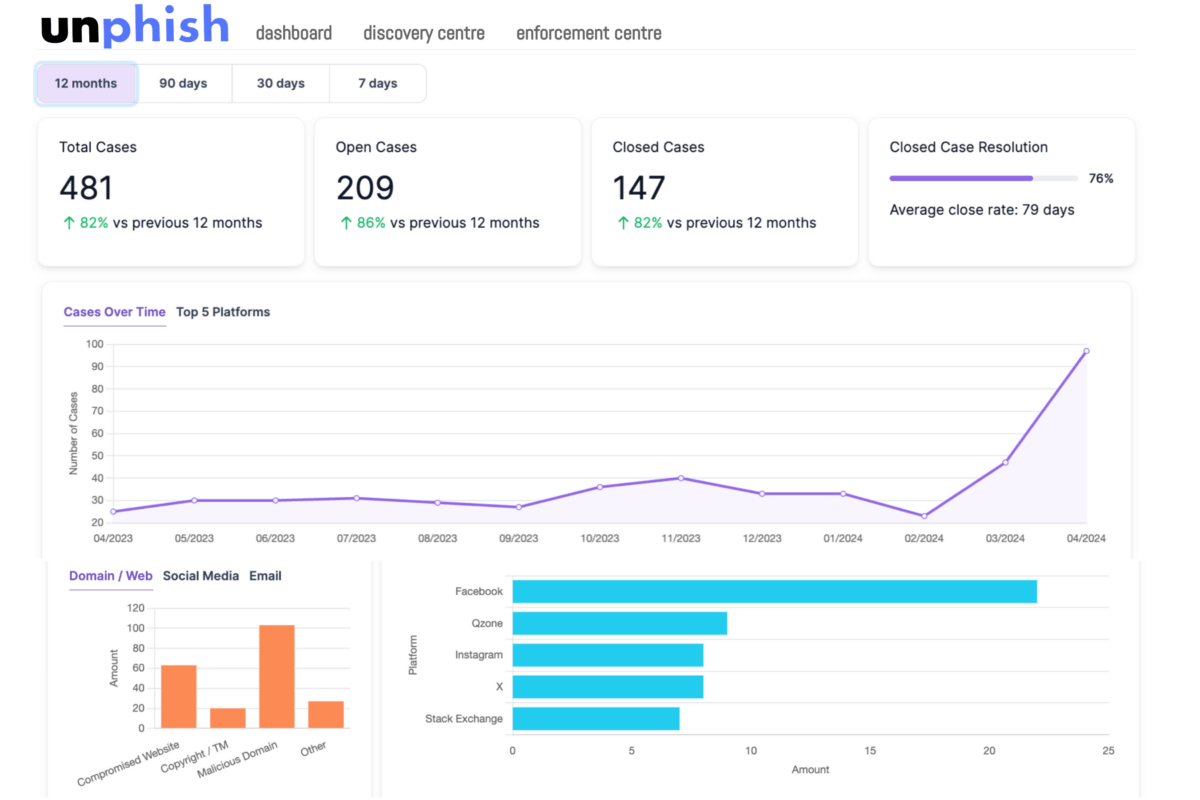
Phishing is a Growing and Omni-Channnel Problem

13 Million
Malicious domain names registered every month

1.62M (Up 20%)
Phishing web sites (attacks) detected in q1 2023

55%
of phishing websites use targeted brand names

12%
of all phishing attacks are deployed thru social media



Challenges with reporting phishing attacks
Platform Diversity: Brands face the challenge of understanding and complying with the distinct policies and procedures of multiple platforms, which vary widely in how they handle reports of phishing and fraudulent activity.
Slow Response Times: Platforms often have slow response times to take-down requests, which can allow fake sites and accounts to remain active and continue causing damage for extended periods.
Policy & Legal Complexity: Pursuing legal action against phishing properties requires navigating a complex web of= laws, policies and regulations, adding layers of difficulty and delay.
Inconsistent Enforcement: There is a lack of consistency in how rules are applied across different platforms, leading to unpredictable outcomes for enforcement efforts.
Resource Intensity: The time and effort required to stay on top of enforcement, given the complexity of managing multiple platforms and continuously evolving threats, demand significant ongoing commitment from brands.
Brand Damage: Each fraudulent site or account can cause significant reputational damage to a brand, and slow take-down processes exacerbate this impact.
The Unphish Journey and our Exciting Roadmap
Unphish (beta) - Phase 1
Unphish Phase 1 introduces a platform with a modular design and an intuitive interface, equipped with a comprehensive suite of tools.

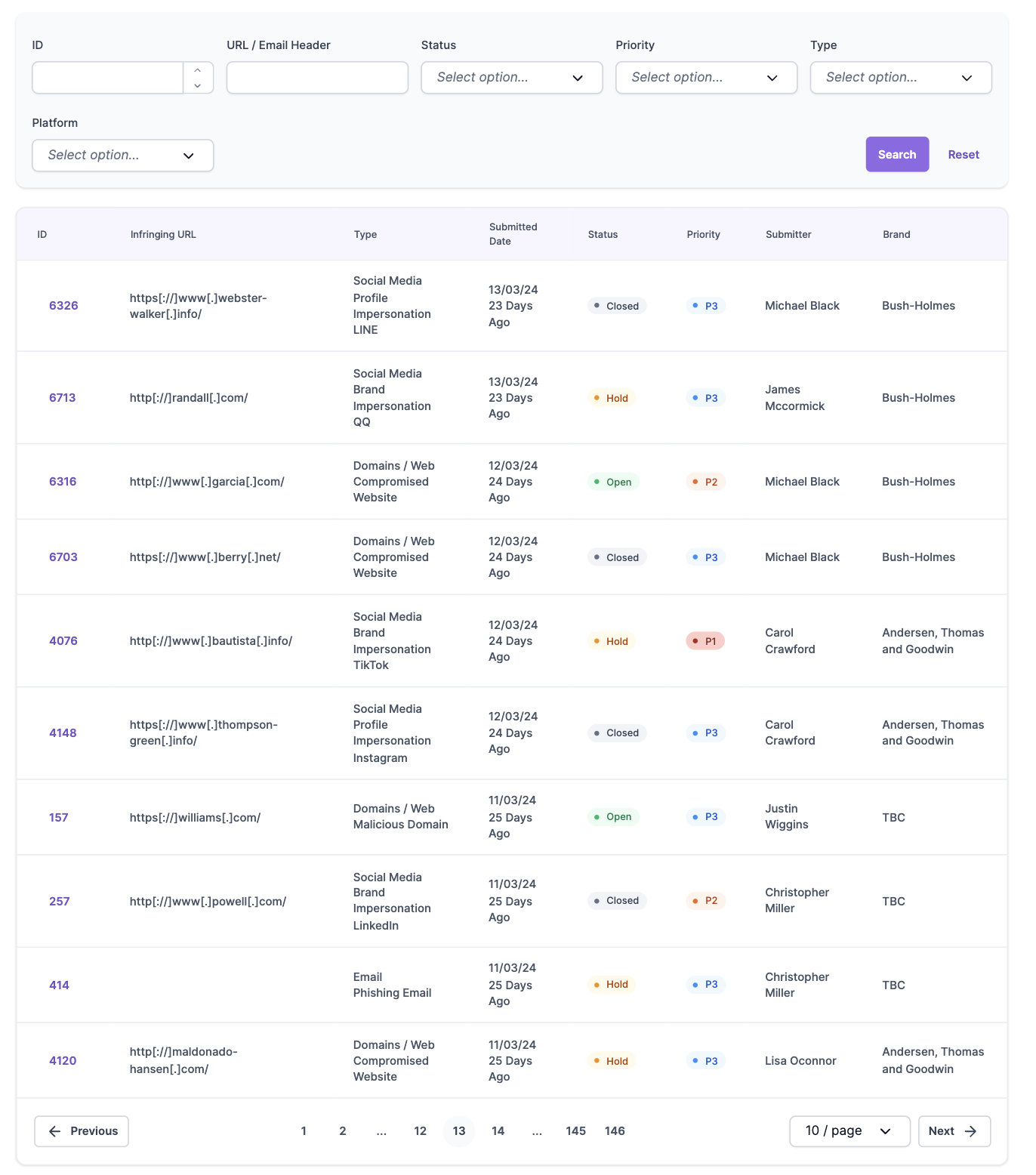
The Enforcement Centre enables brands to manage threats across various platforms and facilitates meticulous documentation and reporting of cases. Clients can explore each infringement in detail, accessing information such as screenshots, metadata, actions taken, and detailed notes, which provide deep insights into each case.

Our Analytics Dashboard delivers in-depth analytics, giving clients a macro view of their threat environment. This includes data on different threats over time, platform hot spots, caseload analytics, and highlights the most common types of issues a client may encounter. This intelligence clarifies the “what”, “why”, “when”, “where”, and “how” of attacks against your brand.

We are also excited to announce the upcoming launch of the Infringement Centre, a streamlined solution for identifying, reporting, and managing online brand infringements. Leveraging multiple threat intelligence sources, it detects malicious activities across domains, web, and social media, offering options to enforce, hold, or ignore these infringements.
Automating Enforcement - Phase 2
For the future development phases of Unphish, the main objective is to create a fully automated platform that streamlines and enhances the process of identifying and managing digital infringements. Here’s a breakdown of what these future phases aim to achieve:

Automated scanning and identification of potential infringements across various digital platforms.

Intelligent analysis of detected content to assess and categorize the nature and severity of infringements

Automatic creation of detailed reports based on the analysis, tailored to specific requirements.

Automated submission of takedown requests to relevant platforms based on predefined criteria.

Smart Case Management Full lifecycle management of each case from discovery to resolution, including updates and status tracking.

Deep Macro and Micro Analysis A dvanced analytical capabilities that provide both industry insights and detailed case examination

Smart Enforcement Ecosystem - Phase 3
Unphish Phase 3 introduces AI and an extended API environment to further automate and streamline the enforcement process

Integration of AI and Machine Learning The platform will integrate an AI layer that intelligently builds submissions based on specific infringement scenarios and the requirements of different platforms. This will ensure that each submission is optimized for higher success rates in enforcement actions.

Extensive API Ecosystem: Unphish will feature a robust API ecosystem that allows for seamless integration with domain registrars, hosting services, and social media platforms. This connectivity will enable the platform to automate processes across a broader network, making workflows more efficient and responsive.

Deep Data Analytics The platform will utilize deep data analysis to offer comprehensive insights into brand-related attacks, trends in industry-specific infringements, and country-specific data. This will enable users to understand the landscape of digital threats more profoundly and tailor their protective measures more effectively.
Issues Unphish Address
Impersonation on the web
Malicious Domains
Unphish actively targets fake social media profiles where malicious actors impersonate senior executives, staff members, or individuals with significant public presence and large social media followings. By leveraging our comprehensive understanding of various platforms' Terms of Service and impersonation policies, we collaborate closely with social media platforms to proactively identify and remove pages and profiles that fraudulently replicate these individuals. This approach not only prevents the spread of misinformation but also protects the identity and reputation of the people being impersonated, ensuring a safer online environment for both public figures and their followers.
Compromised Websites
Unphish addresses compromised websites by capturing all critical data necessary to manage the case effectively. The platform features advanced workflows that facilitate coordination with web hosting providers and website owners, aiming to remove infringing content swiftly. This process not only ensures the removal of harmful material but also helps secure the compromised web environments, preventing them from posing any further threats. Through this structured approach, Unphish enhances the security and integrity of online presences.
Web Copyright Trademark Issues
Unphish efficiently gathers all necessary data to formulate precise DMCA or copyright or trademark infringement notices by scanning websites for infringing content and capturing relevant metadata and content details. This compiled information enables Unphish to generate detailed infringement notices, which are then directly submitted to the content hosts and website owners. By streamlining the process and providing clear documentation, Unphish facilitates prompt communication and effective resolution, ensuring the swift takedown of infringing content while adhering to legal standards and protecting copyright holders' rights.

Issues Unphish Address
social media Impersonation
Fake Social Media Accounts
Unphish proactively addresses the issue of fake corporate accounts by shutting down unauthorized social media accounts that impersonate official corporate brands, effectively preventing them from misleading customers and harming brand reputations. Our approach utilizes sophisticated workflows and a deep understanding of major social media platforms' impersonation policies, Terms of Service, and a strong working relationship with the relevant abuse teams. This strategic alignment allows us to efficiently identify, report, and facilitate the rapid removal of these counterfeit accounts, ensuring swift enforcement actions that uphold the integrity of genuine brands.
Fake Social Media Profiles
Unphish actively targets fake social media profiles where malicious actors impersonate senior executives, staff members, or individuals with significant public presence and large social media followings. By leveraging our comprehensive understanding of various platforms' Terms of Service and impersonation policies, we collaborate closely with social media platforms to proactively identify and remove pages and profiles that fraudulently replicate these individuals. This approach not only prevents the spread of misinformation but also protects the identity and reputation of the people being impersonated, ensuring a safer online environment for both public figures and their followers.
Bad Faith Copyright & Trademark Issues
Unphish efficiently gathers all necessary data to formulate precise DMCA or copyright or trademark infringement notices by scanning websites for infringing content and capturing relevant metadata and content details. This compiled information enables Unphish to generate detailed infringement notices, which are then directly submitted to the content hosts and website owners. By streamlining the process and providing clear documentation, Unphish facilitates prompt communication and effective resolution, ensuring the swift takedown of infringing content while adhering to legal standards and protecting copyright holders' rights.
Issues Unphish Address
Other platforms we enforce
Generic Email Phishing Attacks
Phishing email attacks using free services like gmail or hotmail are surprisingly effective. Unphish generic phishing email attacks by working with the provider to quickly suspend phishing email accounts and all other related services.
Fake Reviews and Social Proofing
Attackers use fake reviews and social proof tactics to lend credibility to their phishing schemes. Unphish can employ authenticity checks to spot and report coordinated fake review campaigns and work with the platform to remove inline with their ToS.
Instant Messenger Scams
Instant Messaging has become a hotspot for cybercriminals due to the anonymity it provides. Unphish collaborates with these platforms to ensure that our clients' brands are not being misused or misrepresented. Our in-depth knowledge of their Terms of Service and direct access to abuse teams help expedite the takedown process.
Sensitive Content Leaks
Unphish efficiently tracks and enforces against sensitive data leaks across social media, the web, and instant messaging by leveraging advanced monitoring technology to detect unauthorized disclosures. We identify data indicative of leaks, enabling rapid response and enforcement actions. Collaborating directly with platform abuse teams, Unphish swiftly removes exposed data and secures breached channels, effectively mitigating potential damages.
Fake Ads
Unphish addresses fake advertisements on platforms like Meta Ads through automated sweeps to detect ads that target brands or mislead consumers into phishing schemes. Upon identifying a fraudulent ad, Unphish leverages its understanding of the platform's advertising policies to quickly report and request the removal of deceptive content.
Fake Jobs
Bad actors often exploit the job-seeking process by posting fake job ads to target unsuspecting applicants. These fraudulent listings are designed to appear legitimate, enticing candidates with attractive job offers. Once engaged, applicants may be asked to provide personal information or pay fees for training and job placement that never materializes. This not only leads to financial losses but can also result in identity theft and significant personal disruption.