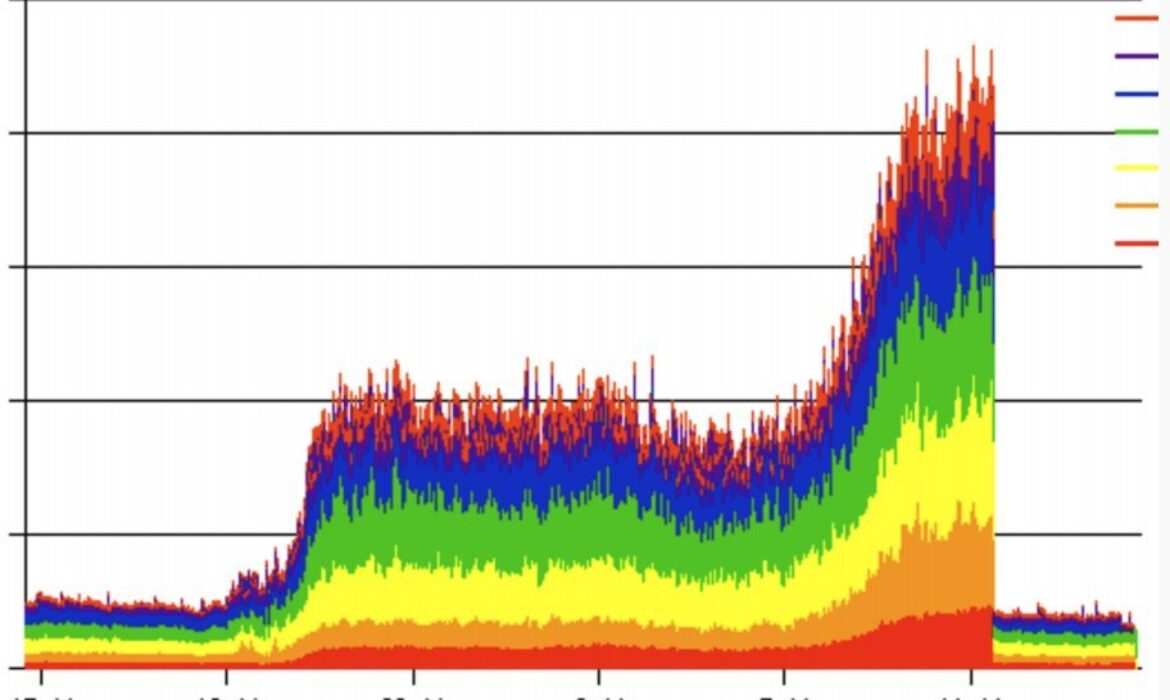
There is a new variation of DDoS attack that allows attackers to target authoritative DNS servers. The vulnerability was identified this week leading to a 50% increase in traffic volume for the .nz authoritative servers. In this case, it was caused by two misconfigured domains, however this helped to identify a potential weakness that could have been exposed by attackers.
The name given to this vulnerability is TsuNAME. It has the potential to impair core internet services. This is particularly concerning because authoritative DNS servers are commonly managed by both government and private organisations, including Internet Service Providers (ISPs) and worldwide tech giants.
TsuNAME is focused on targeting vulnerable recursive resolvers causing them to overwhelm authoritative servers with large amounts of malicious DNS queries. Recursive resolvers are vulnerable when domain names are misconfigured with cyclic dependent DNS records. When vulnerable resolvers access these misconfigurations, they begin repetitively sending malicious DNS queries to authoritative servers.
The issue has subsequently been resolved and the research team have developed CycleHunter, an open-source tool to detect activity of this nature and identify potential future DNS security threats.
This early stage research was conducted by a consortium of researchers through InternetNZ (.nz registry), SIDN Labs, (.nl registry), The Information Science Institute and University of Southern California.
Useful resources to learn more about this attack:
Whitepaper 1: https://tsuname.io/advisory.pdf
Whitepaper 2: https://tsuname.io/tech_report.pdf
Article 1: https://tsuname.io/
About brandsec
Brandsec is a corporate domain name management and brand protection company that looks after many of Australia, New Zealand and Asia’s top publicly listed brands. We provide monitoring and enforcement services, DNS, SSL Management, domain name brokerage and dispute management and brand security consultation services.