

20 February 2023
As the prevalence of domain name-based phishing attacks continues to rise, it has become increasingly important for brands to take proactive measures to protect themselves. One of the most critical steps in this process is the identification and quick resolution of suspicious domain names that could be used by cybercriminals to impersonate the brand and engage in fraudulent activity.
According to the Australian Competition and Consumer Commission’s Scamwatch, Australians reported more than 74,000 phishing attacks with financial losses of more than $24.6 million last year. They estimate that only 13 percent of victims will lodge a report. In this blog, we look at proactive steps brands can take to protect themselves from domain name-based phishing attacks.
Defensive registrations
Domain-based phishing attacks are becoming harder to recognize, and bad actors are becoming more adept at tricking targets with misspellings and variations of a legitimate brand’s domain name. One common tactic used by phishers is to register domain names that are similar to the target brand’s domain name, with slight variations in spelling or extension. For example, a bad actor could target microsoft.com and replace the “m” with “n” to create nicrosoft.com to trick email recipients.
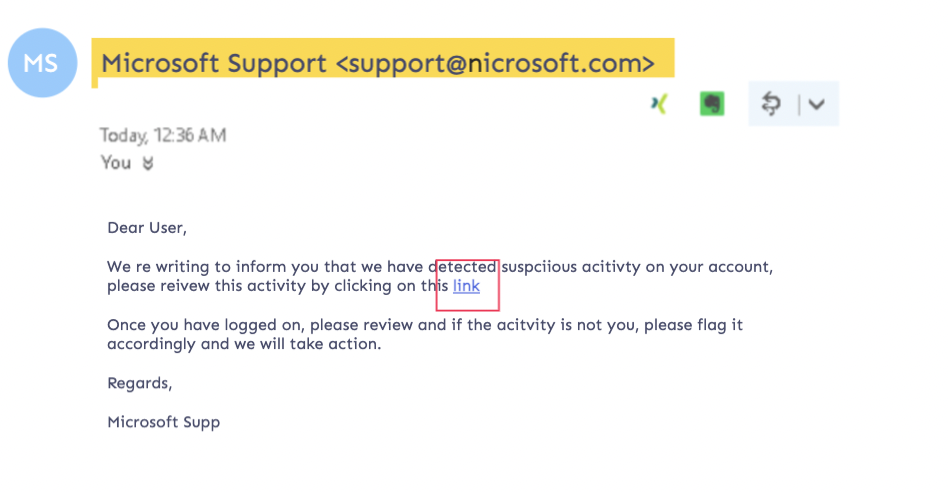
A phishing-based domain name using a misspelling of microsoft.com to trick customers into clicking on a suspicious link.
To develop a typo-spelling defensive domain name registration strategy, consider how your domain name can be altered slightly to trick email recipients or website visitors. Common ways bad actors trick end users by altering the spelling of domain names include:
– Transposing two letters in a domain name, for example, micorsoft.com
– Incorrectly spelling a domain name to make it look like the real domain name, for example, nicrosoft.com
– Registering an identical version of your domain name in another domain name space, for example, microsoft.co or microsoft.com.ai-
– Punycode domains, where bad actors replace English letters with Greek or Acrylic letters, for example, Мicrosoft.com. In this eample, we have used the Greek M in place of the English “m.” These are very hard to detect.
Create a budget, so you don’t get carried away with defensive domain name registrations and focus on the most obvious domain name misspellings. Review annually – It’s important to review how bad actors are changing their registration tactics and make adjustments when new patterns or registration behaviours are detected.
Monitor for suspicious domains
Brands can monitor for newly registered domains that contain their brand name or similar variations. This can be done through automated tools or by conducting regular manual searches. If a suspicious domain is identified, brands can take immediate action to have it taken down.
Our domain name monitoring tool is one of the most comprehensive in the world, covering thousands of domain name spaces and Registry DNS zone files. It identifies cybersquatting, typosquatting, potential phishing domain names, look-alike domains, punycode domains, homographic domains, scam domains, and competitor registrations. Check out our domain monitoring brochure or contact us for a free consultation and basic audit.
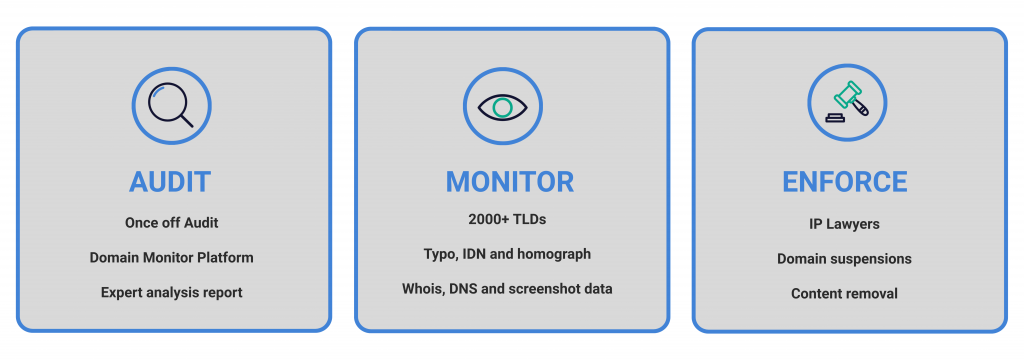
brandsec’s domain monitoring solution
Implement email authentication protocols
Spammers can spoof your domain or organisation to send fake messages that impersonate your organisation. DMARC tells receiving mail servers what to do when they get a message that appears to be from your organisation but doesn’t pass authentication checks or doesn’t meet the authentication requirements in your DMARC policy record. Messages that aren’t authenticated might be impersonating your organisation or might be sent from unauthorised servers.
DMARC is always used with these two email authentication methods or checks:
– Sender Policy Framework (SPF) lets the domain owner authorize IP addresses that are allowed to send email for the domain. Receiving servers can verify that messages appearing to come from a specific domain are sent from servers allowed by the domain owner.
– Domain Keys Identified Mail (DKIM) adds a digital signature to every sent message. Receiving servers use the signature to verify messages are authentic, and weren’t forged or changed during transit.
To understand how brandsec assists our Clients with email fraud defense, check out our brochure.
Educate employees and customers
Educating employees and customers on how to recognise and report phishing attacks can be an effective way to prevent them. This can include providing training on how to identify suspicious emails or websites and encouraging customers to report any suspicious activity related to the brand.
Summary
Overall, a combination of proactive measures such as domain name registration, email authentication, monitoring, and education can help brands to protect themselves from domain name based phishing attacks.
As the prevalence of domain name based phishing attacks continues to rise, it has become increasingly important for brands to take proactive measures to protect themselves. One of the most critical steps in this process is the identification and quick resolution of suspicious domain names that could be used by cybercriminals to impersonate the brand and engage in fraudulent activity. In this regard, brands must remain vigilant and stay ahead of the curve by implementing robust measures that allow for the timely detection and elimination of potential threats.
About brandsec
Brandsec is a corporate domain name management and brand protection company that look after many of Australia, New Zealand and Asia’s top publicly listed brands. We provide monitoring and enforcement services, DNS, SSL Management, domain name brokerage and dispute management and brand security consultation services.
