
Sunday 10 July 2022
A subdomain takeover occurs when an attacker gains control over a subdomain of a target domain. Typically, this happens when the subdomain has a canonical name (CNAME) in the Domain Name System (DNS), but no host provides content for it. This either occurs because the domain name owner has not yet set up the service on the sub-domain, or the content hosting service has ended, but the sub-domain name was not deleted.
Subdomain takeover is a high severity vulnerability that can be exploited to take control of a domain and point it to an address managed by attackers. Attacks on this vulnerability are often used to create phishing sites and spread malware.
The Editor of Cystak spent a weekend looking into the issue and the results were alarming:
…I spent some time coding exploits to find major websites that could be affected by the vulnerability. The results were very unexpected, I found more than 200 domains affected by the (subdomain) vulnerability just in 2 days. These domains belonged to big technology, finance companies and major newspapers.
Subdomain takeover attack Example
The goal of this attack is to point a victim’s domain to an attacker’s address. This is closely related to the domain resolutions have described above. In the case of using A/AAAA records for the resolution, it’s not worth mentioning but the remaining cases have weaknesses.
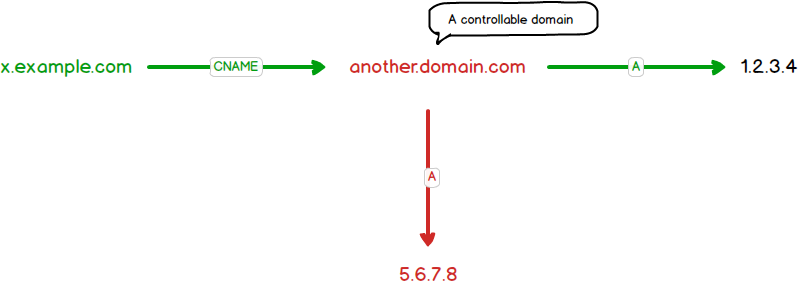
Let’s look at a scenario as follows:
- You own
x.example.com x.example.compoints toanother.domain.comby using a CNAME record
In order to control the content of http://x.example.com, we have to control the content of http://another.domain.com. This is possible, if:
another.domain.comis an expired domain -> Buy this domaindomain.combelongs to Internet service and it allows to create a sub-domain likeanother.domain.comif that name is available. You can find out many services having that feature such as Github, Heroku, Amazon S3, Shopify, etc.
In their review, they found hundreds of subdomains where the domain name hadn’t expired by the hosting service had, and the sub-domain had not been decommissioned. One of the companies identified with this issue was Microsoft.
The method was quite simple. You can find all subdomains using one of many tools online and check the exploitable signature of the sub-domains found. Once a target subdomain was identified it’s just a matter of registering the expired domain name or the service attached to the sub-domain.
How to Protect yourself from subdomain takeovers
Deleting or Expiring Domain Names: Always ensure that before you delete any domain name that all services associated with it, and subdomains, have been deleted and cancelled.
Regular subdomain reviews: Regularly conduct subdomain health checks to make sure all services are current and operational. SubStack will assist to this end and other tools are on the Internet that can assist.
About brandsec
Brandsec is a corporate domain name management and brand protection company that looks after many of Australia, New Zealand and Asia’s top publicly listed brands. We provide monitoring and enforcement services, DNS, SSL Management, domain name brokerage and dispute management and brand security consultation services.

