Brand Protection vs Fraud-as-a-Service
Has brand protection kept up with fast moving and large clone website networks? Whether you’re in retail, banking, or government services, attackers can now deploy hundreds of convincing fake websites in hours — complete with stolen branding, payment or credential-harvesting...
Why Domain Registrars Are Key to Stopping Fast Flux Phishing
A recent Dark Reading article highlighted the continued growth of fast flux phishing, an old tactic that’s been on the radar of enforcement professionals for years. Maybe a forgotten scam for many, those of us working in the phishing takedowns and cyber enforcement space are...
Cheap Domains, Costly Threats: How Cybercriminals Exploit Bulk Registrations
Bulk Domain Registrations: How Criminals Exploit Cheap Domains
How Cybercriminals Exploit Cheap Bulk Registrations
The retail domain name...
Phishing Domains and New gTLDs: A Growing Security Concern
Phishing Domains are a new gTLD problem. The introduction of new generic top-level domains (gTLDs) was intended to create a more diverse and flexible internet landscape, offering greater options for internet users. However, the reality has shown that these new gTLDs have...
.TOP Domain Registry Warned Over Phishing Concerns
.top Registry has been warned by ICANN in relation to the number of phishing domain names registered in the .top domain name space.
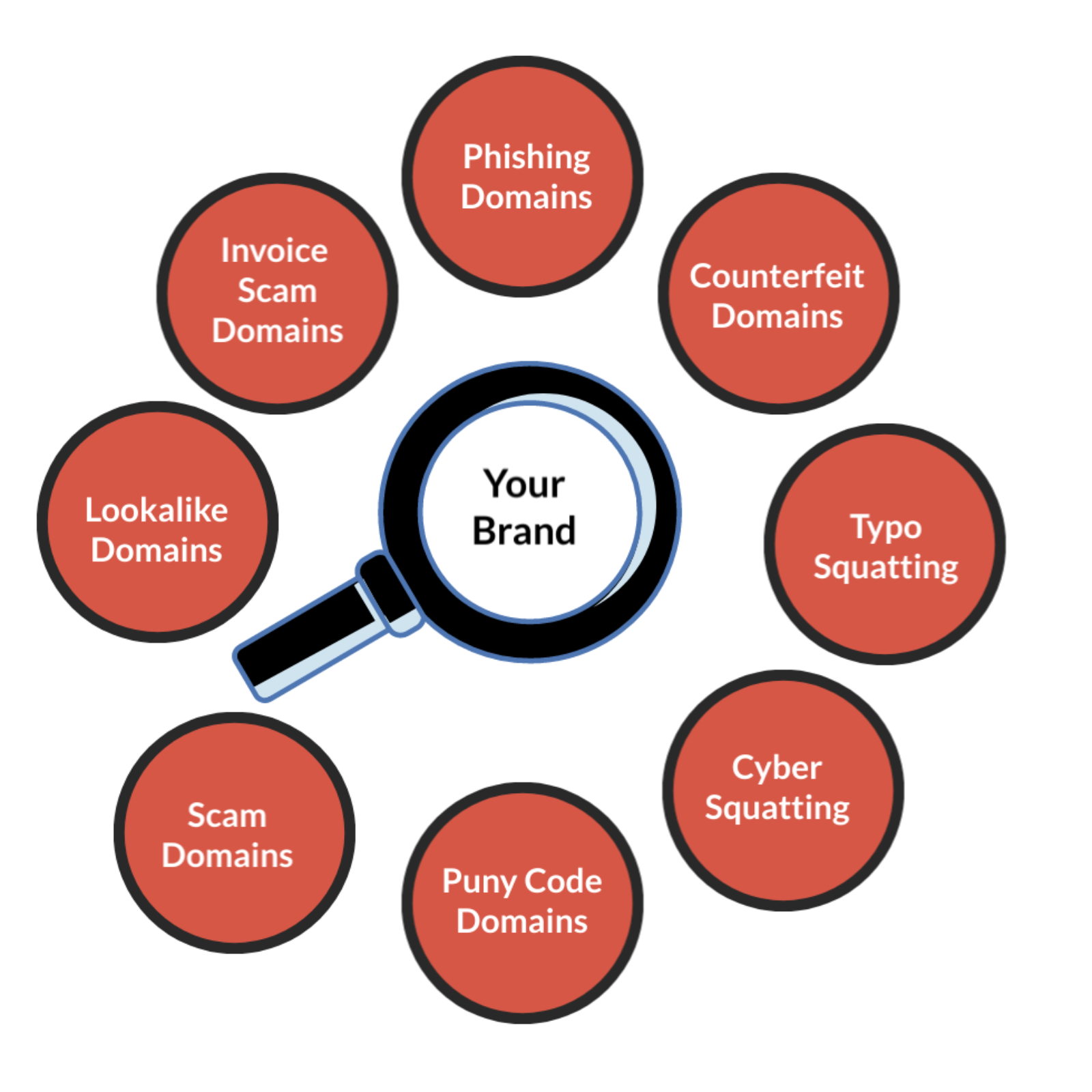
How to monitor for fake websites and social media accounts
Why Monitoring is Essential
protecting your brand from impersonation and fraud is more crucial than ever. Fake websites and social media accounts can cause significant damage to your brand’s reputation and customer trust. Brandsec and...
Website Takedown Strategies: Malicious Domains vs Compromised Websites
Discover takedown strategies for malicious domains and compromised websites.
Learn how to collect evidence, liaise with registrars, & escalate issues.
Phishing: Malicious Domain Names
Phishing: Addressing Malicious Domain Names
Domain registrars are obligated under the Registrar Accreditation Agreement (RAA) to suspend domain names that are specifically set up for phishing purposes. However, our research indicates that brands...
Gaining Market Advantage via Strategic Domain Name Monitoring
In this blog, we look at the critical role of domain name monitoring in both protecting your brand and providing a strategic edge by analyzing competitors’ domain activities to inform smarter business decisions.
Safe Harbor: Implications for Hosting Providers that Ignore Malicious Content
safe harbor protects hosting parties from liability associated with 3rd parties publishing content on their servers, but this protection is not absoloute.
Protecting Against the Threat of Malicious Domain Name Registrations
Malicious domain name registrations are specifically created for nefarious purposes, such as phishing attacks. These registrations are more effectively mitigated at the DNS level compared to domains that have been compromised. Typically, these malicious domains are newer and...
Tactics cyber criminals deploy to evade detection
20 October 2022, by Ed SeafordAvoiding DetectionWeb monitoring tools play an important role in thwarting impersonation and phishing attacks, but cybercriminals deploy an array of evasion techniques to evade detection and carry out their nefarious activities. In my years...